AWS Administrative User: Once you’ve created your AWS account, it’s critical to follow best security practices. The first thing AWS recommends is not to use the root account for everyday tasks. Instead, you should create a dedicated Administrative IAM user with full permissions to manage your AWS resources.
In this guide, we’ll walk through the steps to create an administrative user in AWS, assign permissions, and enable secure access.
Table of Contents
Why Not Use the Root User?
The root user has unrestricted access to your entire AWS account, including sensitive billing information and service limits. Using it regularly increases the risk of accidental or malicious changes.
Best practice: Use the root user only for initial setup and critical tasks, then create a separate IAM user with admin access for daily operations.
Prerequisites
- A valid AWS account.
- Access the AWS Management Console using the root user.
Step-by-Step Guide to Create an AWS Administrative User
Step 1: Sign in as the Root User
- Go to the AWS Console: https://console.aws.amazon.com/
- Sign in using the root user email and password.
Follow this article to create a free AWS account and sign in with the Root user.
Step 2: Open the IAM Service
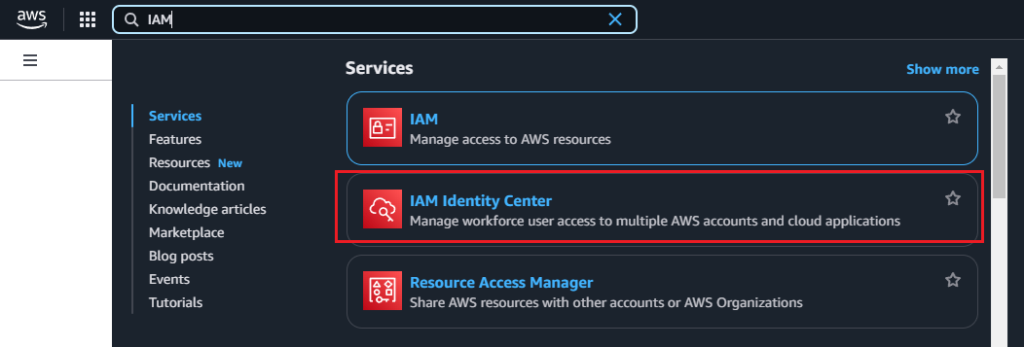
- In the AWS Console, go to the Services menu.
- Search for IAM Identity Center and open it.
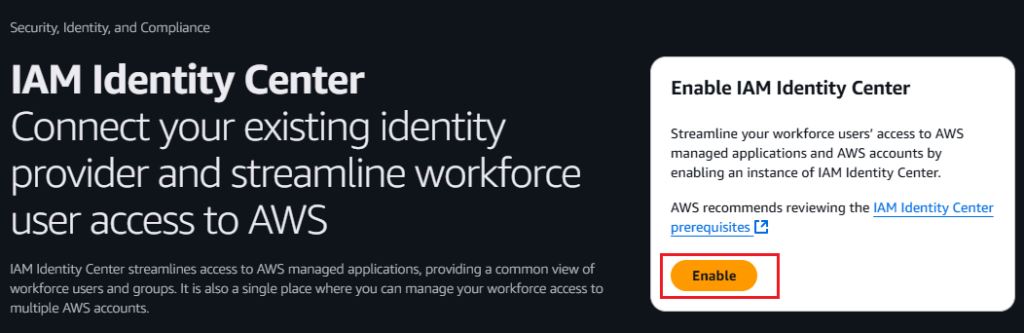
3. Enable IAM Identity Center: Click on the Enable button.
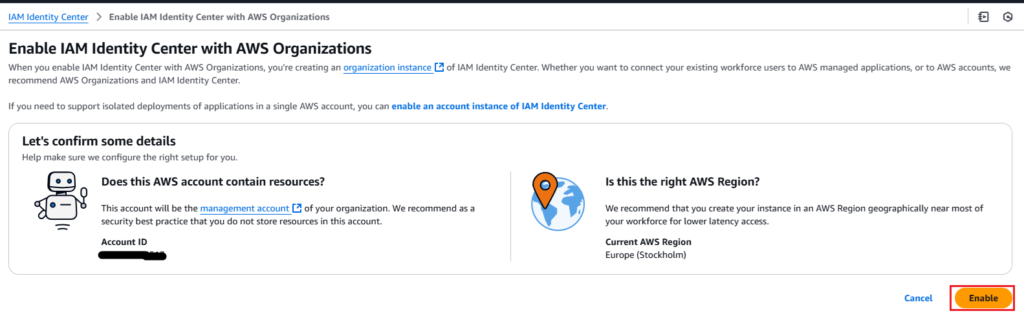
4. Finally, enable it under Enable IAM Identity Center with AWS Organizations.
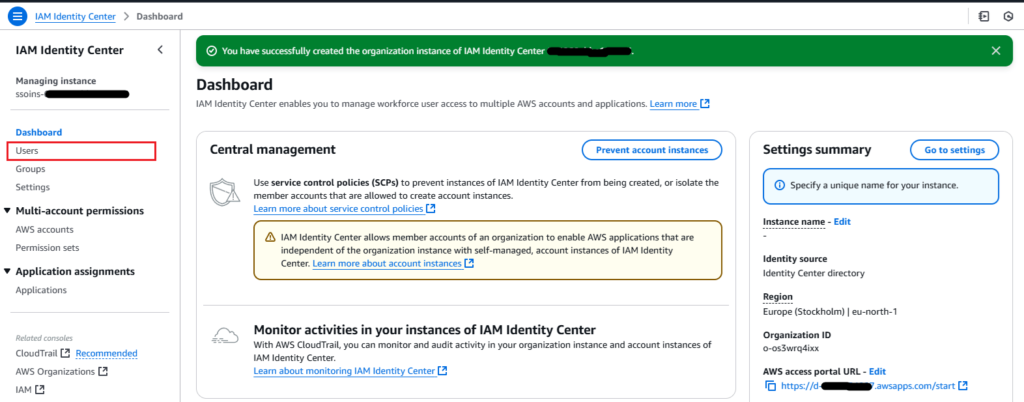
Step 3: Add a New IAM User
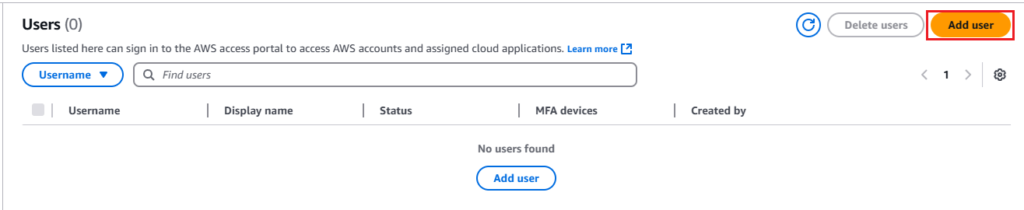
- In the IAM Identity Center dashboard, click on “Users” in the left menu.
2. Click the “Add user” button.
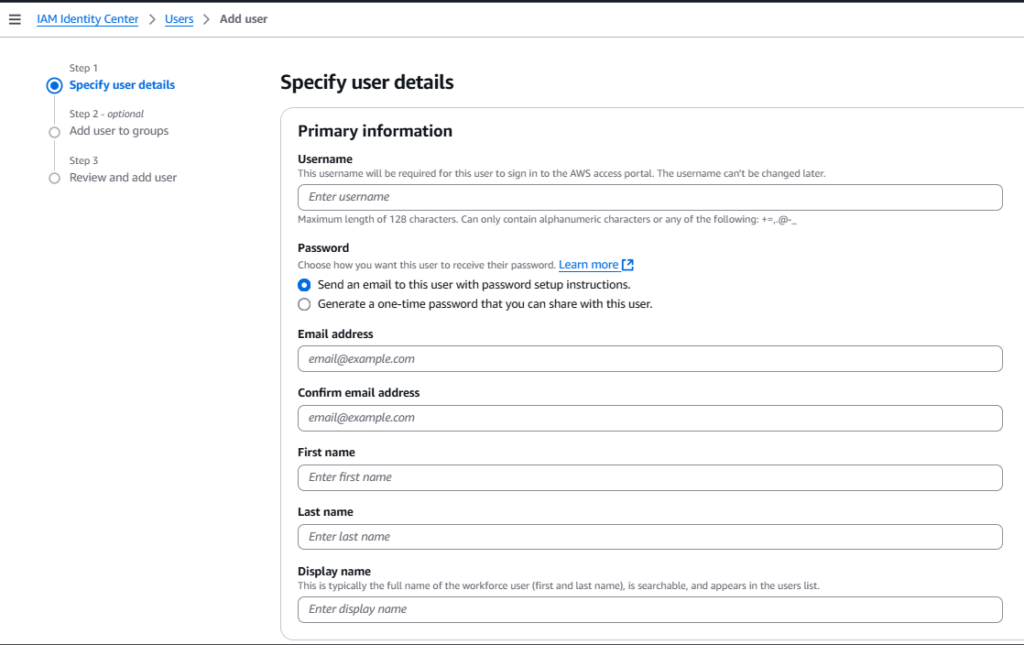
Step 4: Configure User Details
- Enter a username, such as admin.
- Under Password, choose:
- Send an email link to set up a password
- Generate a one-time password
- Enter other user details: Email, First name, Last name, etc.
- Click “Next”.
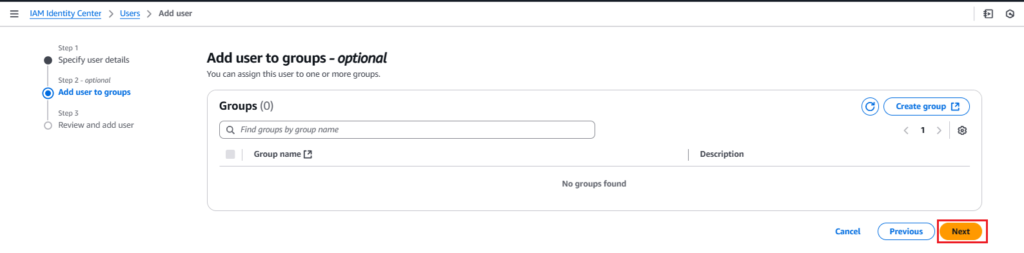
5. Add the user to groups (optional), then click Next.
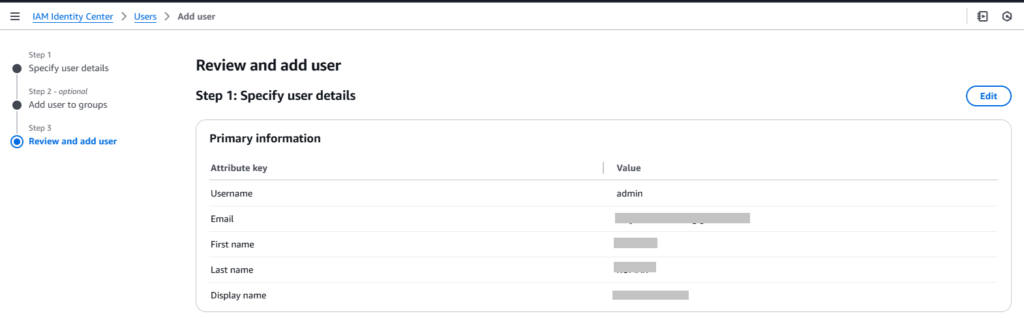
6. Review and add the user.
7. Finally, you will see a successfully added user notification.
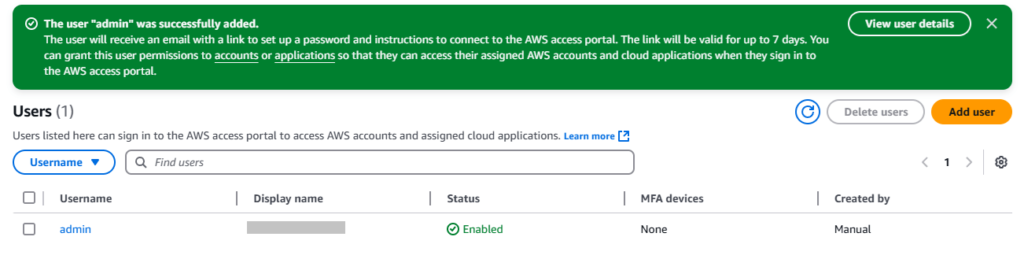
Step 5: Set Permissions
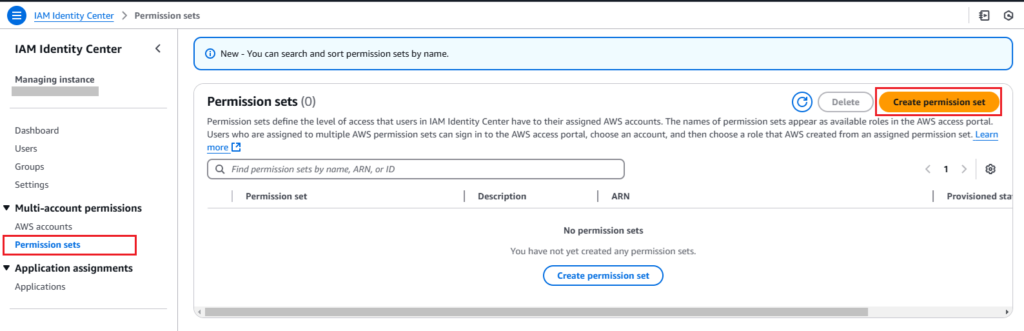
1. In the IAM Identity Center dashboard, click on “Permission sets” in the left menu. After that, click on the “Create permission set” button.
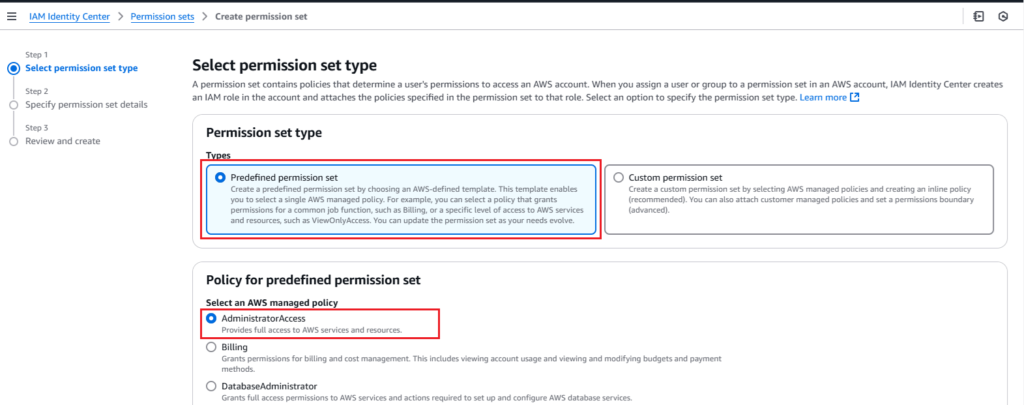
2. Select permission set type and Policy: Choose predefined permission set type and to grant full administrative access, choose AdministratorAccess policy.
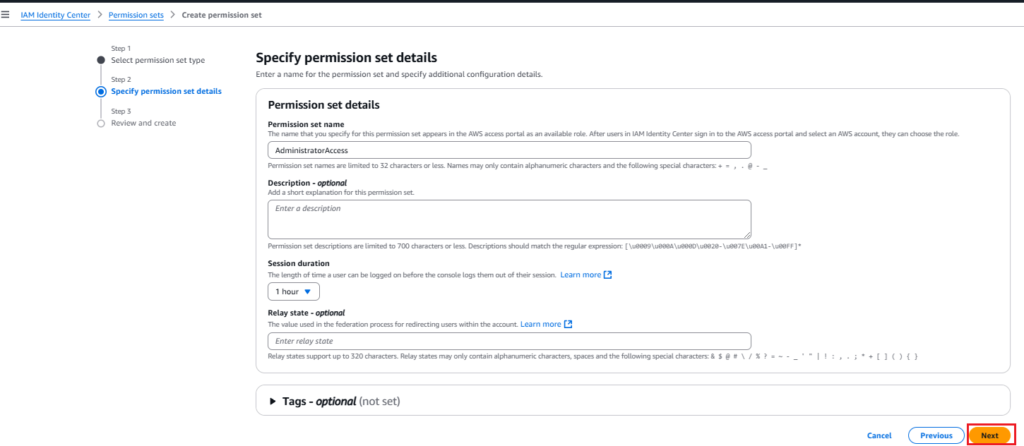
3. Specify permission set details: fill in the name, description, session duration, etc, and click the Next button.
4. Review and create: review the permission set details and click on the Create button. After that, you will see the permission set created successfully with a notification with administrative access.
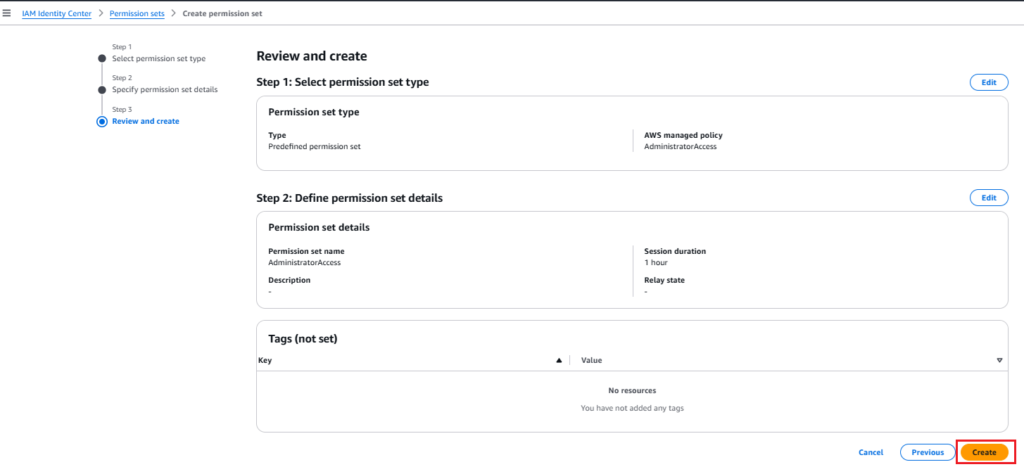
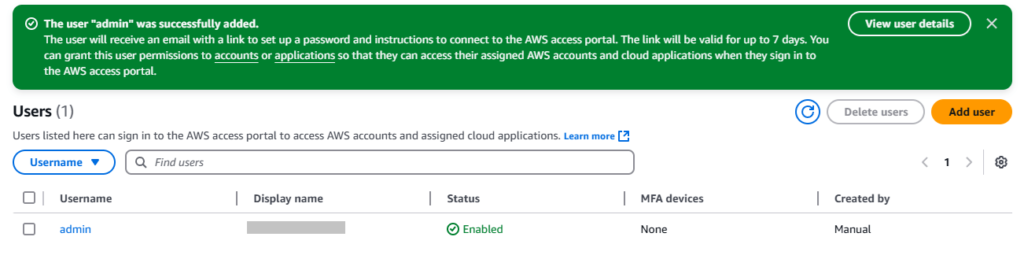
Step 6: Assign users to AWS account and Review
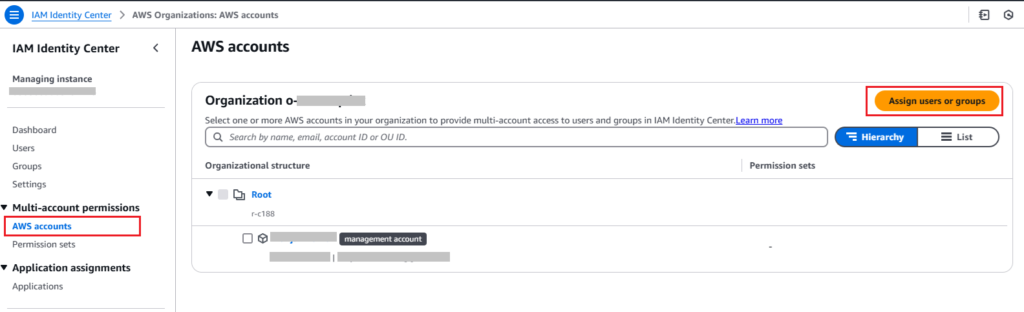
1. In the IAM Identity Center dashboard, click on “AWS accounts” in the left menu. After that, click on the “Assign users or groups” button.
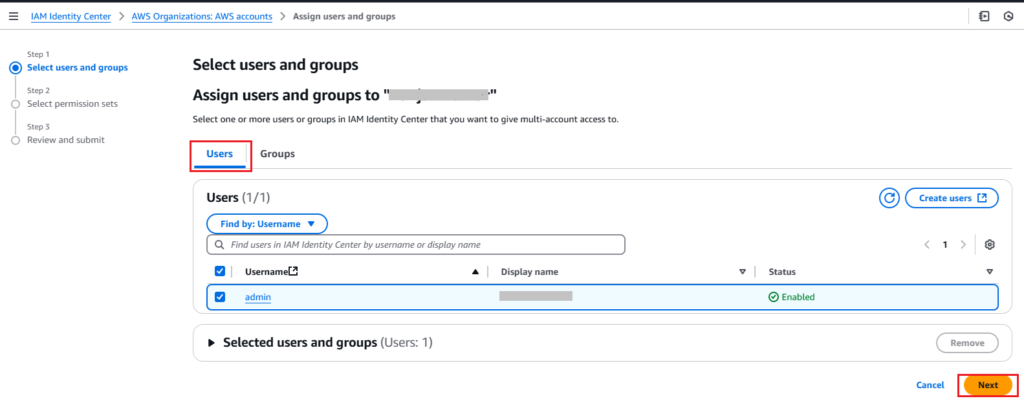
2. Select users and groups: choose created user (admin) here and click Next button.
3. Select permission sets: choose created permission set (AdministratorAccess) here and click the Next button.
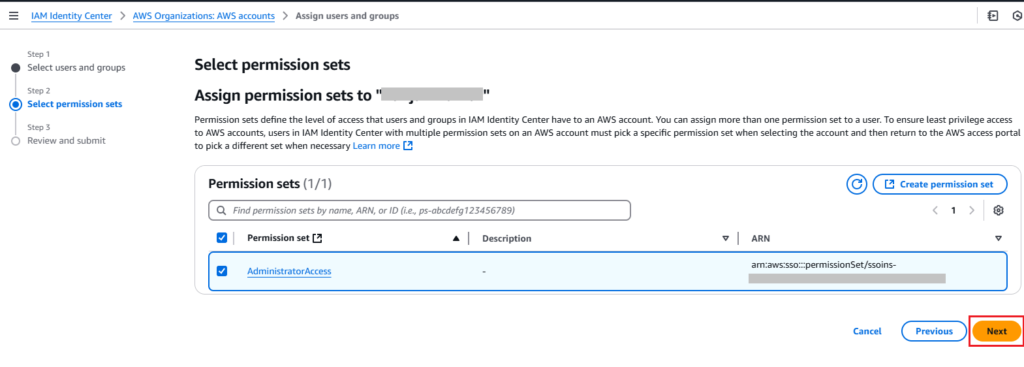
4. Finally, review and submit.
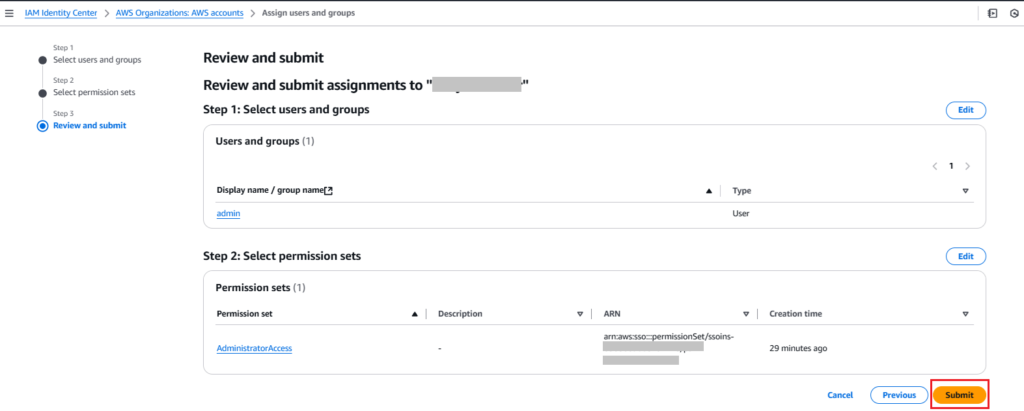
Step 7: Create and Save Credentials
After the user is created, you will see A Sign-in link for the IAM user. Set up the new password here.
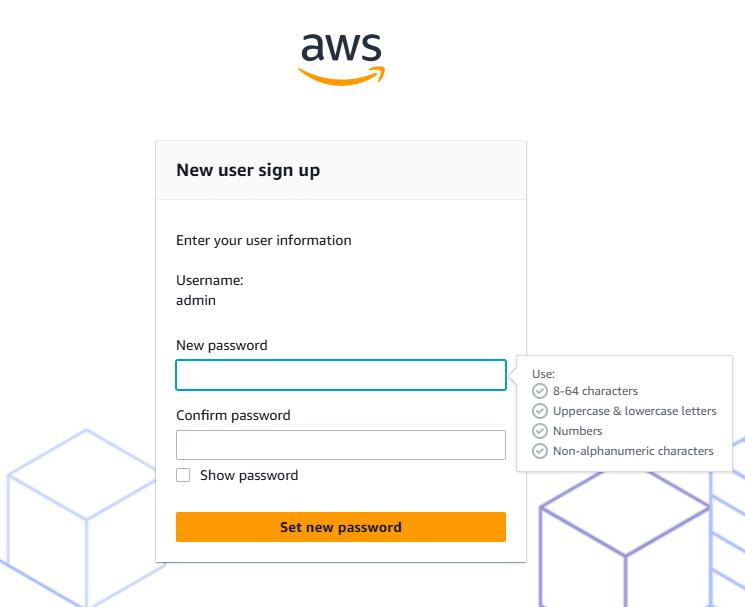
👉 Save these securely! You won’t be able to see the secret access key again.
The IAM user can now access the AWS Console at:
https://[your-account-alias].signin.aws.amazon.com/console
Extra Security Steps (Recommended)
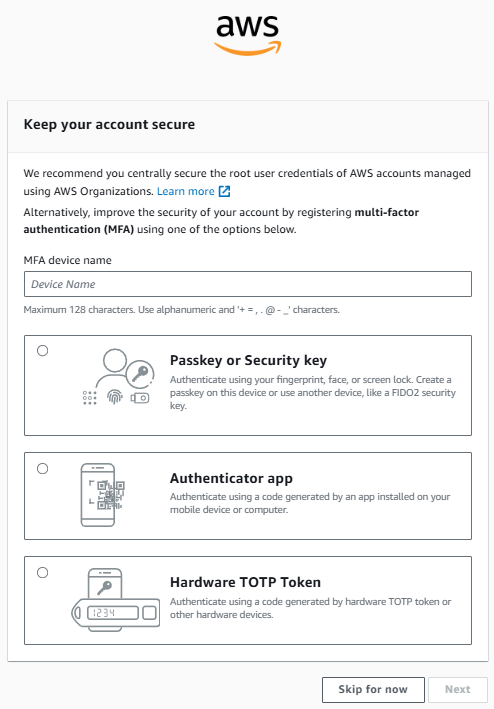
Enable MFA (Multi-Factor Authentication) for IAM User
- Go to IAM > Users.
- Click on the IAM username.
- Select the “Security Credentials” tab.
- Click “Assign MFA device” and follow the instructions to set up using an authenticator app like Google Authenticator or Authy.
Create an Account Alias
This makes your IAM sign-in URL easier to remember:
- Go to IAM > Dashboard.
- Click on “Customize” next to the Account Alias section.
- Enter a custom name, such as
mycompany-admin.
Your new IAM login URL will be: https://mycompany-admin.signin.aws.amazon.com/console
Conclusion
Creating an AWS administrative user is a critical first step in securing your AWS account. With this in place, you can safely manage AWS resources without exposing the powerful root account to everyday risks.
Remember:
- Use the root user only when necessary.
- Secure all IAM users with MFA.
- Monitor usage with IAM policies and CloudTrail.
